CTI: A Build of Materials for a Cyber Threat Intelligence Program
A long form post (+audio) covering a set of resources to help you along your journey.
Want to listen?
Given how long this post is - you’ve got a few options to listen in audio form.
Use your favorite reading tool i.e. Substack App or Readwise.
Use Microsoft Edge ‘Read Page’ functionality.
Listen to the 16min Google NotebookLM conversation I’ve thrown together using this post and its noted resources. Attached right at the top of this post.
Using Google NotebookLM’s conversation feature is extremely interesting - even though it can feel ‘static’ and over enthusiastic at times, its an avenue we might explore for future posts. Enjoy! But please… continue reading…
Intro
Developing, establishing, measuring and maturing a Cyber Threat Intelligence Program is no simple out of the box feat! If you’ve been in the intelligence space for any period of time either directly from an operational perspective or from the side lines as a consumer or observer - it’s very much still a mix of art, craft and science.
A CTI Program is unique to every organization, the region and most importantly the stakeholders who drive the CTI Program ‘Requirements and Direction’ - so a simple ‘One Size Fits All’ approach is unlikely to be suitable.
We all have nuances to work with!
The notion of M1019 comes from MITRE ATT&CK and is to be acknowledged as a mitigation against certain techniques… but it’s more than just that; its as ambiguous as it is defined.
“A threat intelligence program helps an organization generate their own threat intelligence information and track trends to inform defensive priorities to mitigate risk”
https://attack.mitre.org/mitigations/M1019/
In this long form post, I’ll do my best based on personal research, interest and education in the intelligence space to help break the ice and define a build of materials (set of resources) that might be helpful if your looking to get started in designing or operating a Cyber Threat Intelligence Program.
A cheat sheet I would have found valuable if I was starting from scratch, and definitely useful even on-going as a refresher of helpful non-exhaustive resources.
This post is not going to tell you how to build and deliver a CTI Program - you will still need to do the hard work!
Knowing of the unknown, makes it known!
’Obvious Person’
The build of materials
To make this article hopefully of instant value, please refer to the resource linked.
But of course, please keep reading for now.
So where to get started?
First - remind yourself that this is no out of the box solution for a CTI Program.
A program is going to be specific to the organization, the industry, the people, the stakeholders, the requirements, the direction, the intent, the tech stack, the funding and most definitely the expectations.
My advice is leverage the three stages of this proposed Build of Materials.
[1] READ: Understand, Determine and Decide
Give yourself ample time to get educated! Regardless if your a seasoned pro - and even if your looking to commence a CTI Program or deliver/mature an existing one - you have to take the time and let the organization know that you need to educate first and foremost.
Education isn’t really just about reading, watching videos or consuming content like this - its more so about enabling yourself time to absorb information relating to CTI concepts, models, frameworks, structures, innovations etc. and determine how or what explicitly applies to the organization and stakeholders, and then talk amongst peers, leaders, stakeholders, about their expectations and or understanding.
Think of it as also a method to baseline the organization.
Take notes, brainstorm, mind map, do all the stuff - to help cut down and determine and decide your direction of attack. Remember, keep things simple!
To help govern this approach it’s highly recommend setting a ‘Mission Statement’.
Set a Mission Statement
I spoke heavily in my last post around ‘Mission Statements’ take a read (later).
A mission statement greatly applies to a CTI Program.
If we use MITRE ATT&ACK M1019 description of a Threat Intelligence Program we can condense this down to:
“Inform defensive priorities to mitigate risk”
This - in its simplest form, is a suitable mission statement for a CTI Program for ANY organization to anchor themselves to! You could almost say, that by default this is what ANY organizations CTI Program is aiming for. Useful when communicating with industry peers.
A key core deliverable then of the Program is that you should anchor yourself to this mission statement at all times, with all decisions.
Coming back to this simple statement and validating that the program either in concept or practice is able to or is achieving this outcome at the most valuable point within the organization where change and risk mitigation can occur; then the program may lead to success.
Example
If we’ve determined that we are a ‘intelligence warehouse’ whereby our focus is on tactical and technical outputs i.e. Threat Feeds (IoC heavy) for our stakeholders - then we would fail our mission statement objective if we thought it was of value to provide threat feed / IoC heavy technical reports to Executive parties; where as instead these reports (alongside the curated Threat Feeds) are better suited for operational stakeholders such as the SOC, NOC or DFIR whereby risk mitigation can occur.
Initial Pitfalls
When starting your CTI Program journey or building on an existing one; your going to stumble and come across many initial pitfalls, the big thing here is to not get caught up at these points, and progress on through.
Some of the pitfalls that you might initially come across are as follows:
Not taking the time to be educated and informed.
Not being familiar with how the organizations Cyber Security practices, capabilities etc. are architected or operate.
Not taking the time to determine the organization needs for CTI outputs.
Over complicating it all!
Setting deliverable expectations too high.
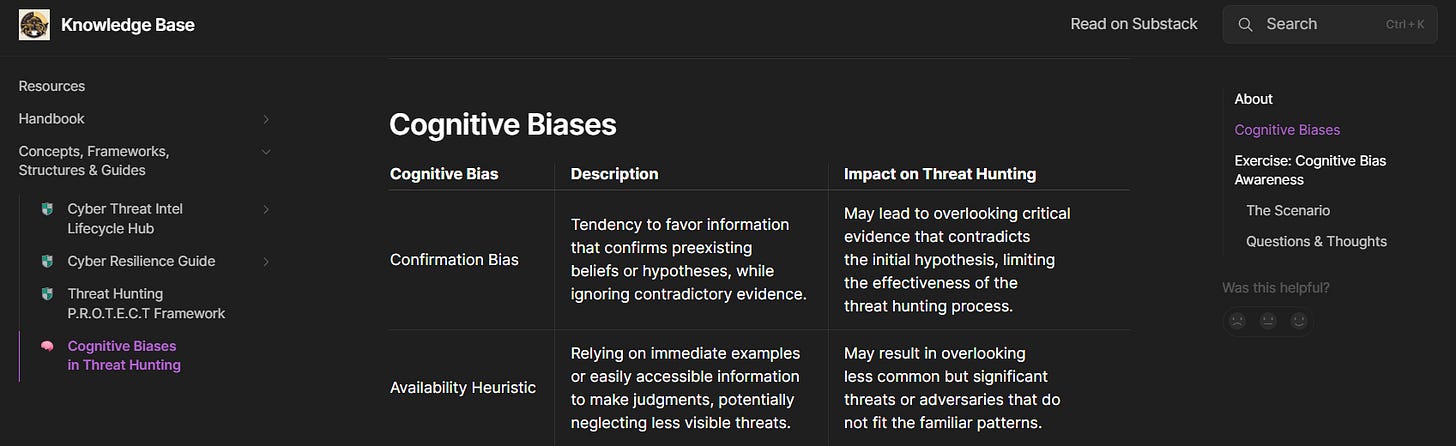
Additionally, a post that I wrote a while back though focused on Threat Hunting, still applies here which is cognitive biases. Take a read (later).
You can also find the helpful matrix on the M1019 Gitbook page.
Cognitive Biases can occur at any stage; so it’s important to determine and understand when you may come across this points of conflict and how to navigate appropriate around them for the value of the CTI Program.
Don’t aim for perfect!
A pitfall when commencing anything like establishing, delivering, maturing or fixing an existing Cyber Threat Intelligence Program is trying to aim for perfection across a broad range of deliverables and objectives.
A CTI Program is a significant undertaking, never aim for perfection but focus on providing 'value' and if you can, stage out your ‘value’ elements across a timeline.
Example
If the organization and stakeholders most crucial Priority Intelligence Requirement (PIR) is to have effective (timely) monitoring for mentions of their organization on data breach forums, obfuscated sites and such; then there is no direct immediate need to apply effort to other lower value PIRs before determining that this collection capability exists within the CTI Program.
Being able to deliver confidently on the most crucial PIRs set by stakeholders above everything else; is essential.
Perhaps, you determine that without additional funding, service onboarding, resourcing etc - the most crucial PIRs are not achievable in the expected timeframes.
Be conscious that external factors (people and things) might try and lead you to over complexicising (sure that’s a word) your deliverable objective.
Remember that it is more important to deliver what stakeholders absolutely, crucially require - and if these expectations cannot be met based on collection gaps, skill gaps, technology and funding gaps - then be upfront with stakeholders initially that perhaps the program in its current form can only deliver on 65% of what is being expected and project what is needed to achieve a more desired result.. i.e. funding, tooling, skills gap bridging etc.
Always be realistic!
[2] DEVELOP: Design, Define and Measure
As mentioned at the ‘READ’ initial phase - Visualization helps! Making use of flow charts, mind maps and diagrams, sticky notes, are valuable to help understand how these opensource resources, frameworks, models and common practice methodologies, organization and stakeholder requirements, funding etc. can all come together.
A while back I posted about a conceptual high-level diagram of a possible CTI Program Build of Materials utilizing the freely available resources mentioned.
And just like all things within the IT space, we have an endless supply of credible, freely available resources (plus AI) we just need to define what is essential to us and get some agreeable wins on the board.
“Not everything can be useful, Not everything useful can be of value, Not everything of value is going to answer your problem… Just get started”
HERMIT-m1019
The Pareto Principal
Cliché, but going to mention it. The Pareto Principal or the 80/20 Rule, makes sense to embrace when working on a CTI Program journey. As at the end of the day we want to achieve our mission statement, and we want to provide value at the most impactful area within the organization.
Therefor during the DEVELOP phase, you may wish to employ this model of thinking…
What is going to give me 80% of the desired end state, with 20% of the upfront effort?
Doing this might just help, cut out the noise of ‘its all too much’ and allow you to drill into the core foundational aspects of the CTI Program.
Alignment & Validation
Take your design ideas and core deliverable objectives for the program and draw it out to help elicit context and suitability to what you are aiming to deliver on overall for the organization and stakeholders.
You might uncover gaps, pitfalls, wants rather than needs or just outright limitations based on funding, technical expertise or tooling and so forth.
As you commence designing, defining and setting measures for the CTI Program (new or existing) its around this time that you start to pull on the existing knowledge and education collected earlier on and expanding on that by using the additional resources listed in the ‘Build of Materials’.
You are at a stage where you should have a somewhat clear understanding of the direction you are aiming to go and can start to see how the CTI Program aligns with the organization and can start seeking points of validation from those that matter before going too much further on the journey.
Cyber Threat Intelligence is a mixture of Art, Craft and Science.
[3] BUILD: Establish, Grow and Adjust
Your at the final section of the build of materials, but in all reality your journey has just commenced (another cliché moment… sorry)
Putting it all together!
The resources set out in this section may help with forming some level of consistency, structure and overall alignment to a model well known in the Cyber Threat Intelligence space; that being the Lifecycle Model.
A post written many moons ago details how the use of the Cyber Threat Intelligence Lifecycle as a form of hierarchical schema/taxonomy - maybe a beneficial approach to organizing the day-to-day activities associated with a CTI Program.
As you possible already know or in time may learn to know and understand when working with CTI is that - approaches must always be systematic and process orientated.
Things need to be catalogued, organized, tracked, measured and maintained - therefor creating taxonomies and schema’s for structure are not just for show but they do provide ongoing value across the lifespan of the CTI Program as illustrated also in resources like the CTI-CMM and CU-GIRHs, let alone MITRE ATT&CK.
Remain Nimble
A Cyber Threat Intelligence Program is ongoing, ever changing, always adapting and developing, sometimes the requirements may shrink, other times they may grow - you have to adapt, evolve and adjust as things happen.
You have to stay nimble and be open to change.
Requirements are going to change over time and its important that we remove our biases and foster working with a CTI Program that adopts change and challenges, and builds resilience along the way.
Ensure that your CTI Program is not too rigid, not too restricted, not too over-cooked; allow there to be an acceptable level of flexibility and adaptability as you iterate through it’s forever changing variations the organization, stakeholders and threat landscape will demand.
A Final Thought
During the wild ride of developing, establishing, measuring and maturing a Cyber Threat Intelligence Program, remember to come back to the core anchor point - the Mission Statement, to keep the CTI Program on track with delivering what is set out to do.
“Inform defensive priorities to mitigate risk”
Start with simple! Don’t over-complicate.
Focus on the most crucial requirement that will make the most impact in meeting the mission statement outcome.
Iterate, evolve and mature.
And as always, stay proactively educated at every corner… till next time…